As a graphical user interface is useless in case of routers and switches, it looks useful when configuring a firewall. Of course it is my point of view. I do not go into what is better for you. I like using CLI but, sometimes, it is worth to simplify your daily routine. The first step is to configure HTTPS access to webUI of USG6300. This is what we will focus today.
Well known topology from the last post:
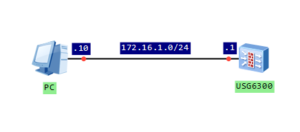
Configure IP address of firewall’s interface and add it to trust zone:
[USG6300]interface GigabitEthernet 0/0/7 [USG6300-GigabitEthernet0/0/7]ip address 172.16.1.1 24 [USG6300]firewall zone trust [USG6300-zone-trust]add interface GigabitEthernet 0/0/7
Enable HTTPS server on that interface:
[USG6300]interface GigabitEthernet 0/0/7 [USG6300-GigabitEthernet0/0/7]service-manage https permit
Create two administrator’s accounts:
#
manager-user web_lab
password cipher %@%@`ruiCXfgEFCJGnNu0!<@&bYP@.eMJIk7-H&m&h&[xo11Oh_Z%@%@
service-type web
level 15
ftp-directory hda1:
ssh authentication-type password
ssh service-type stelnet
#
manager-user web_lab_2
password cipher %@%@S0e84!g|rRX38&1S*-l;h*!ub`{@$-`o0=71fW<8Ch{9g0'"%@%@
service-type web
level 15
ftp-directory hda1:
ssh authentication-type password
ssh service-type stelnet
#
Why two accounts? Because we will assign different roles for these 2 administrators to show you such possibility. We will use the default system-admin role for one administrator and a new created web-admin role for the second one.
# role system-admin description system-admin dashboard read-write monitor read-write policy read-write object read-write network read-write system read-write # role web_lab dashboard none monitor read-only session statistic statistic-acl none packet-capture diagnose policy none object none network none system none #
Then we can bind our administrators to properly defined roles:
[USG6300-aaa]bind manager-user web_lab role system-admin [USG6300-aaa]bind manager-user web_lab_2 role web_lab
Enable HTTPS server with default certificate and set the service port:
[USG6300]web-manager enable Enable http server successfully ! [USG6300]web-manager security enable port 8443 Enable http security-server successfully ! web-manager
Let’s verify what will happen if we use both accounts to get to GUI of the firewall.
Open a browser and enter https://172.16.1.1:8443.
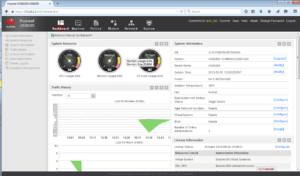
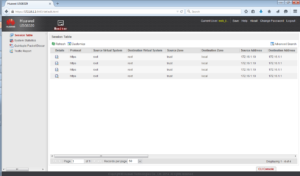
As you can notice, the access varies depending on the assigned role for administrators.
 Labnario Huawei From Scratch
Labnario Huawei From Scratch