So far you have learned basic and selective QinQ on Huawei swiches. They seem like a simple Layer 2 VPN solution, which we can use to connect 2 or more offices. And of course, it is truth.
But, sometimes, we want to have an access to external services or just to the Internet, instead of connecting 2 branch offices. And, still we can use QinQ technology, why not?
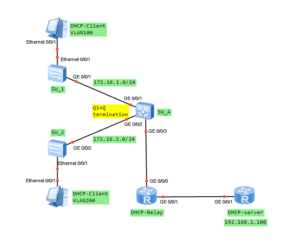
The only thing we should do is to terminate QinQ VLAN Tag on a router. Just create L3 subinterface and let the router to use IP routing table to forward packets.
In our LAB, I am going to show you how to terminate QinQ to use DHCP server, located outside our network. In this case DHCP Relay feature must be used.
So let’s get to the point!
 Labnario Huawei From Scratch
Labnario Huawei From Scratch