If you want to recall how to configure GRE, just look at GRE on Huawei routers.
You can return to IPSec configuration, reading IPSec on Huawei AR router.
Today, I’m going to put them together and try to configure GRE over IPSec.
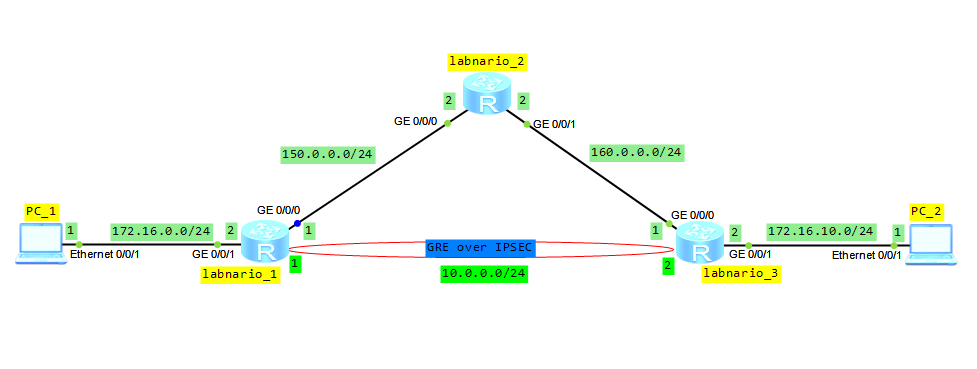
Based on the topology below, configure IP adresses and OSPF protocol to ensure connectivity between all routers (omitted here).
Configure tunnel interface on labnario_1 and labnario_3:
[labnario_1]interface Tunnel0/0/0 [labnario_1-Tunnel0/0/0] ip address 10.0.0.1 255.255.255.0 [labnario_1-Tunnel0/0/0] tunnel-protocol gre [labnario_1-Tunnel0/0/0] source 150.0.0.1 [labnario_1-Tunnel0/0/0] destination 160.0.0.1 [labnario_3]interface Tunnel0/0/0 [labnario_3-Tunnel0/0/0] ip address 10.0.0.2 255.255.255.0 [labnario_3-Tunnel0/0/0] tunnel-protocol gre [labnario_3-Tunnel0/0/0] source 160.0.0.1 [labnario_3-Tunnel0/0/0] destination 150.0.0.1
Use ping command to check if the tunnel interface has been set up:
[labnario_3]ping 150.0.0.1
PING 150.0.0.1: 56 data bytes, press CTRL_C to break
Request time out
Reply from 150.0.0.1: bytes=56 Sequence=2 ttl=254 time=50 ms
Reply from 150.0.0.1: bytes=56 Sequence=3 ttl=254 time=30 ms
Reply from 150.0.0.1: bytes=56 Sequence=4 ttl=254 time=30 ms
Reply from 150.0.0.1: bytes=56 Sequence=5 ttl=254 time=40 ms
--- 150.0.0.1 ping statistics ---
5 packet(s) transmitted
4 packet(s) received
20.00% packet loss
round-trip min/avg/max = 30/37/50 ms
Configure IPSec on labnario_1 and labnario_3 (labnario_3 configuration is omitted here):
[labnario_1]acl 3500
[labnario_1-acl-adv-3500]rule permit gre source 150.0.0.1 0 destination 160.0.0.1 0
[labnario_1]ipsec proposal labnario
[labnario_1]ike local-name labnario_1
[labnario_1]ike peer labnario_3 v1
[labnario_1-ike-peer-labnario_3]exchange-mode aggressive
[labnario_1-ike-peer-labnario_3]local-id-type name
[labnario_1-ike-peer-labnario_3]pre-shared-key cipher labnario
[labnario_1-ike-peer-labnario_3]remote-name labnario_3
[labnario_1-ike-peer-labnario_3]remote-address 160.0.0.1
[labnario_1]ipsec policy labnario 1 isakmp
[labnario_1-ipsec-policy-isakmp-labnario-1]security acl 3500
[labnario_1-ipsec-policy-isakmp-labnario-1]ike-peer labnario_3
[labnario_1-ipsec-policy-isakmp-labnario-1]proposal labnario
[labnario_1-GigabitEthernet0/0/0]ipsec policy labnario
<labnario_1>dis ike sa
Conn-ID Peer VPN Flag(s) Phase
---------------------------------------------------------------
11 160.0.0.1 0 RD|ST 2
10 160.0.0.1 0 RD|ST 1
Flag Description:
RD--READY ST--STAYALIVE RL--REPLACED FD--FADING TO--TIMEOUT
HRT--HEARTBEAT LKG--LAST KNOWN GOOD SEQ NO. BCK--BACKED UP
<labnario_1>dis ipsec sa
===============================
Interface: GigabitEthernet0/0/0
Path MTU: 1500
===============================
-----------------------------
IPSec policy name: "labnario"
Sequence number : 1
Acl Group : 3500
Acl rule : 5
Mode : ISAKMP
-----------------------------
Connection ID : 11
Encapsulation mode: Tunnel
Tunnel local : 150.0.0.1
Tunnel remote : 160.0.0.1
Flow source : 150.0.0.1/255.255.255.255 47/0
Flow destination : 160.0.0.1/255.255.255.255 47/0
Qos pre-classify : Disable
[Outbound ESP SAs]
SPI: 2472318789 (0x935c9745)
Proposal: ESP-ENCRYPT-DES-64 ESP-AUTH-MD5
SA remaining key duration (bytes/sec): 1887436800/3557
Max sent sequence-number: 0
UDP encapsulation used for NAT traversal: N
[Inbound ESP SAs]
SPI: 3680592061 (0xdb6160bd)
Proposal: ESP-ENCRYPT-DES-64 ESP-AUTH-MD5
SA remaining key duration (bytes/sec): 1887436800/3557
Max received sequence-number: 0
Anti-replay window size: 32
UDP encapsulation used for NAT traversal: N
Finally, configure static routes that inject traffic from PC1 and PC2 into tunnel interface:
[labnario_1]ip route-static 172.16.10.0 255.255.255.0 Tunnel0/0/0 [labnario_3]ip route-static 172.16.0.0 255.255.255.0 Tunnel0/0/0
Let’s verify whether traffic between hosts, passing through tunnel interface, is encrypted by IPSec (use ping between PC1 and PC2):
<labnario_1>dis ipsec statistics esp Inpacket count : 844 Inpacket auth count : 0 Inpacket decap count : 0 Outpacket count : 852 Outpacket auth count : 0 Outpacket encap count : 0 Inpacket drop count : 0 Outpacket drop count : 0 BadAuthLen count : 0 AuthFail count : 0 InSAAclCheckFail count : 0 PktDuplicateDrop count : 0 PktSeqNoTooSmallDrop count: 0 PktInSAMissDrop count : 0
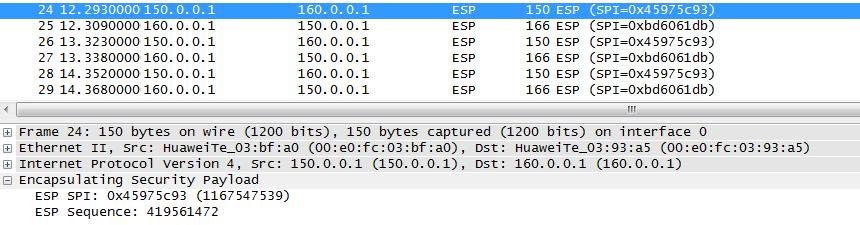
Now we can try to spy captured packets between PCs:
 Labnario Huawei From Scratch
Labnario Huawei From Scratch