We have to remember that traffic policy consists of 3 parts:
- Classifier
- Behavior
- Traffic-policy
In brief, to configure a traffic policy:
- define traffic class
- define action to be applied to the traffic class
- associate traffic classifiers and behaviors
- apply the traffic policy to an interface.
Let’s start from ACL.
We have possibility to configure many rules in an ACL. If the ACL is specified in if-match clause, then a packet is matched against multiple rules. If the packet matches a rule in the ACL, then it stops checking against the next rules.
- In a case of DENY action in the ACL, the matched packet is denied, regardless of what traffic behavior defines.
- When PERMIT action is defined in the ACL, then traffic behavior is applied to the matched packet.
Let’s focus on if-match clauses now and matching order between them.
We have 2 possibilities to configure a traffic classifier:
- With logic OR relationship between multiple matching rules
- With logic AND relationship between multiple matching rules.
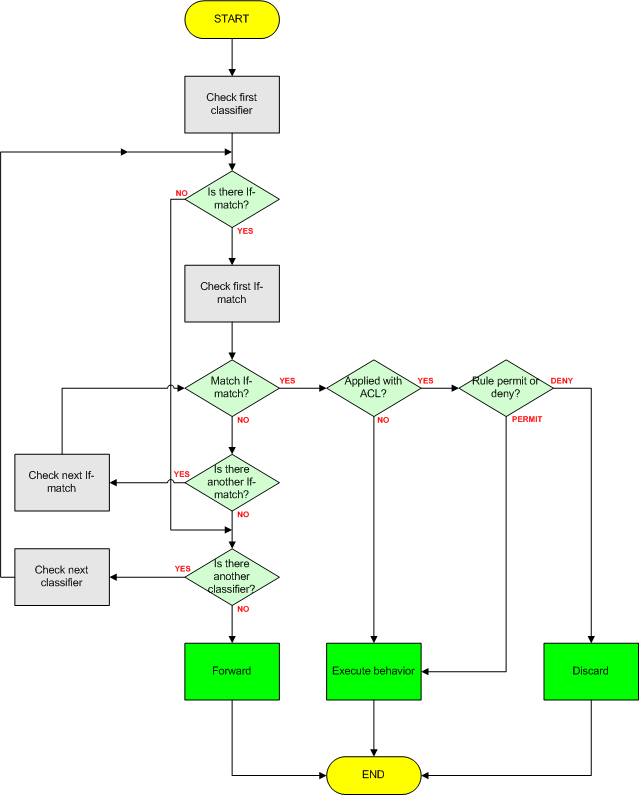
In the flowchart you can see traffic policy implementation with logic OR:
Notice that traffic behavior is applied for the packets that match any one of the if-match clauses. In this situation, packet is matched against If-match clauses, in the order of the If-match clauses configuration. This kind of traffic classifier is commonly used.
In logic AND implementation, the device combines all if-match clauses and then processes the combination of if-match clauses according to the procedure of logic OR. If one of the if-match clauses is applied with ACL, each rule of the ACL is combined with all of the other if-match clauses. In this situation, the order of if-match clauses does not impact on the final matching result.
As you know, one or more classifiers and behaviors can be configured in a traffic policy. A packet is matched against traffic classifiers in the order, in which those classifiers have been configured. If the packet matches a traffic classifier, no further match operation is performed. If not, the packet is matched against the following traffic classifiers one by one. If the packet does not match traffic classifiers at all, the packet is forwarded with no traffic policy executed.
Anyway, the order of traffic classifier can be changed by the following command:
classifier classifier-name behavior behavior-name precedence precedence
Let’s try to configure a traffic policy as follows:
- packets coming from source IP address 10.1.1.0/24, with DSCP 18, are then remarked as AF31
- packets coming from source IP address 172.16.1.0/24, with DSCP 18, are discarded
- other packets are forwarded directly.
# acl number 3000 rule 5 permit ip source 10.1.1.0 0.0.0.255 dscp af21 rule 10 deny ip source 172.16.1.0 0.0.0.255 dscp af21 # traffic classifier labnario operator or if-match acl 3000 # traffic behavior labnario remark dscp af31 # traffic policy labnario classifier labnario behavior labnario # interface GigabitEthernet0/0/0 traffic-policy labnario inbound
I have a home task for you. Try to configure the same policy but using logic AND. Your traffic policy must do the same like the one configured.
Unfortunately, awards are not provided 😉
I will publish the solution soon on Facebook.
All comments (solutions) are welcome.
 Labnario Huawei From Scratch
Labnario Huawei From Scratch