Simple Network Management Protocol (SNMP) is widely used for IP networks’ devices management and monitoring. Not only routers and switches can be managed using SNMP. It can be used with servers, modems, printers, etc. It is application layer protocol and is defined as IETF standard.
How SNMP works?
It operates based on the following components:
- Network Management Station (NMS), sends SNMP requests to query managed devices and receives alarms send by these devices. NMS uses the MIB to identify and manage device objects.
- Agent – process running on the managed device which is responsible for sending alarms to the NMS and processing requests received from NMS.
- Managed device – a networking device on which the Agent process is running.
It is also important to remember, that community string is used in SNMPv2c to identify communication between NMS and Managed device. Community string is a kind of password which is send as a clear-text string. Using community we can restrict access to our managed device.
SNMP configuration example:
To enable SNMP agent on the managed device:
<labnario>system-view [labnario]snmp-agent
Let’s check if our SNMP agent is running:
[labnario]display snmp-agent sys-info
The contact person for this managed node:
R&D Beijing, Huawei Technologies co.,Ltd.
The physical location of this node:
Beijing China
SNMP version running in the system:
SNMPv3
As you see, SNMPv3 agent is enabled by default. The contact person and physical location, both have some default information configured. To run SNMPv2c only, we have to disable SNMPv3:
[Huawei]undo snmp-agent sys-info version v3
Let’s check again:
[Huawei]display snmp-agent sys-info
The contact person for this managed node:
R&D Beijing, Huawei Technologies co.,Ltd.
The physical location of this node:
Beijing China
SNMP version running in the system:
SNMPv2c
To change the equipment administrator’s contact information:
[labnario]snmp-agent sys-info contact Call labnario at 00-11 223344556677
[labnario]snmp-agent sys-info location Warsaw, Poland
[labnario]display snmp-agent sys-info
The contact person for this managed node:
Call labnario at 00-11 223344556677
The physical location of this node:
Warsaw, Poland
SNMP version running in the system:
SNMPv2c
Now we want our agent to be managed by the NMS. To do so, we need to configure community for read only and/or read-write access. First we need to configure access-list, which allows access for our NMS station:
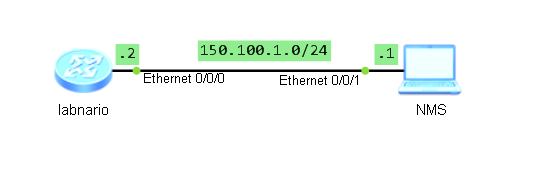
[labnario]acl 2012 [labnario-acl-basic-2012] [labnario-acl-basic-2012]rule 10 permit source 150.100.1.1 0.0.0.0
Now we can configure access for NMS host defined in ACL 2012:
[labnario]snmp-agent community read LABNARIO_COMMUNITY_RO acl 2012
If we want our NMS station not only to browse but also modify MIB objects, read-write access rights should be configured:
[labnario]snmp-agent community write LABNARIO_COMMUNITY_RW acl 2012
Now our agent can be pooled by the NMS station. Both read only and read-write access rights are configured. If we do not want some MIB objects to be modified by the NMS, MIB view needs to be defined and applied to the previously configured community string:
[labnario]snmp-agent mib-view excluded LIMITED-VIEW1 1.3.6.1.4.1.2011.6.7 [labnario]snmp-agent community write LABNARIO_COMMUNITY_RW acl 2012 mib-view LIMITED-VIEW1
Now we want to configure our agent to send alarms to the NMS. In this example we use traps, for inform messages just use ‘inform’ parameter instead of ‘trap’.
[labnario]snmp-agent target-host trap address udp-domain 150.100.1.1 params securityname LABNARIO
Parameter ‘securityname’ is the name for the principal on whose behalf SNMP messages will be generated.
Now enable the function of sending traps to NMS. After this function is configured, the device reports abnormal events to the NMS:
[Huawei]snmp-agent trap enable Warning: All switches of SNMP trap/notification will be open. Continue? [Y/N]:y
This function has to be configured in both trap and inform modes.
You can also enable traps for specific features:
[Huawei]snmp-agent trap enable feature-name ? arp Enable ARP traps bfd Enable BFD traps bgp Enable BGP traps bulkstat Enable BULKSTAT traps configuration Enable CONFIGURATION traps datasync Enable DATASYNC traps dhcp_trap Enable dhcp_trap e-lmi Enable E-LMI traps efm Enable EFM traps eoam-1ag Enable EOAM-1AG traps eoam-y1731 Enable EOAM-Y1731 traps etrunk Enable E-Trunk traps
Final configuration:
[labnario]displ curr | inc snmp snmp-agent snmp-agent local-engineid 800007DB03548998AE0B48 snmp-agent community read LABNARIO_COMMUNITY_RO acl 2012 snmp-agent community write LABNARIO_COMMUNITY_RW mib-view LIMITED-VIEW1 acl 2012 snmp-agent sys-info contact Call labnario at 00-11 223344556677 snmp-agent sys-info location Warsaw, Poland snmp-agent sys-info version v2c undo snmp-agent sys-info version v3 snmp-agent target-host trap address udp-domain 150.100.1.1 source LoopBack0 params securityname LABNARIO v2c snmp-agent mib-view excluded LIMITED-VIEW1 hwCfgChgNotify snmp-agent trap source LoopBack0 snmp-agent trap enable
Verification:
[labnario]display snmp-agent community
Community name:LABNARIO_COMMUNITY_RO
Group name:LABNARIO_COMMUNITY_RO
Acl:2012
Storage-type: nonVolatile
Community name:LABNARIO_COMMUNITY_RW
Group name:LABNARIO_COMMUNITY_RW
Acl:2012
Storage-type: nonVolatile
[labnario]displ snmp-agent mib-view viewname LIMITED-VIEW1
View name:LIMITED-VIEW1
MIB Subtree:hwCfgChgNotify
Subtree mask:FFF0(Hex)
Storage-type: nonVolatile
View Type:excluded
View status:active
[labnario]displ snmp-agent target-host
Target-host NO. 1
-----------------------------------------------------------
IP-address : 150.100.1.1
Source interface : LoopBack0
VPN instance : -
Security name : LABNARIO
Port : 162
Type : trap
Version : v2c
Level : No authentication and privacy
NMS type : NMS
With ext-vb : No
-----------------------------------------------------------
[labnario]displ acl 2012
Basic ACL 2012, 1 rule
ACL's step is 5
rule 10 permit source 150.100.1.1 0 (0 times matched)
 Labnario Huawei From Scratch
Labnario Huawei From Scratch

Налаштування SNMP на Huawei
snmp-agent sys-info version v2c
snmp-agent community read pmon123
snmp-agent community write privatepmon123
snmp-agent target-host trap-hostname PMONSERVER address 192.168.10.10 udp-port 162 trap-paramsname PMON_SRV
snmp-agent target-host trap-paramsname PMON_SRV v2c securityname PMON_SRV
snmp-agent trap enable standard
https://pmon.com.ua/post/24