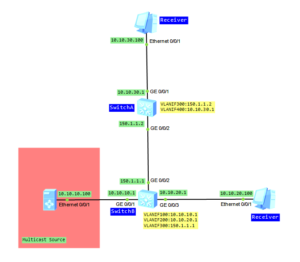
Last time IP FRR on Huawei routers was introduced. Let’s go on with VPN FRR today.
- Configure IP addresses based on the topology (omitted)
- Configure ISIS on PE1, PE2 and PE3.
- Configure MPLS function on all PE routers and enable MPLS LDP to set up an LSP.
- Configure VPN instance on all PE devices.
- Configure MP-IBGP between PE routers.
- Configure EBGP between CE and PE2/PE3 routers.
- Configure VPN FRR policy on PE1.
- Configure BFD session between PE1 and PE2.
Configure ISIS and MPLS globally and on interfaces (PE1 as an example):
[PE1]isis
[PE1-isis-1]is-level level-2
[PE1-isis-1]network-entity 10.0010.0100.1001.00
[PE1-isis-1]
[PE1]mpls
[PE1-mpls]quit
[PE1]mpls ldp
[PE1-mpls-ldp]
[PE1]interface GigabitEthernet0/0/1
[PE1-GigabitEthernet0/0/1]isis enable
[PE1-GigabitEthernet0/0/1]mpls
[PE1-GigabitEthernet0/0/1] mpls ldp
[PE1-GigabitEthernet0/0/1]quit
[PE1]interface GigabitEthernet0/0/2
[PE1-GigabitEthernet0/0/2]isis enable
[PE1-GigabitEthernet0/0/2]mpls
[PE1-GigabitEthernet0/0/2] mpls ldp
[PE1-GigabitEthernet0/0/2]quit
[PE1]interface LoopBack0
[PE1-LoopBack0]isis enable
[PE1]dis isis peer
Peer information for ISIS(1)
System Id Interface Circuit Id State HoldTime Type PRI
-------------------------------------------------------------------------------
0020.0200.2002 GE0/0/1 0020.0200.2002.01 Up 7s L2 64
0030.0300.3003 GE0/0/2 0030.0300.3003.01 Up 8s L2 64
Total Peer(s): 2
[PE1]dis mpls ldp peer
LDP Peer Information in Public network
A '*' before a peer means the peer is being deleted.
------------------------------------------------------------------------------
PeerID TransportAddress DiscoverySource
------------------------------------------------------------------------------
2.2.2.2:0 2.2.2.2 GigabitEthernet0/0/1
3.3.3.3:0 3.3.3.3 GigabitEthernet0/0/2
------------------------------------------------------------------------------
TOTAL: 2 Peer(s) Found.
Configure VPN instance on all PE devices (PE1 as an example):
[PE1]ip vpn-instance labnario
[PE1-vpn-instance-labnario]route-distinguisher 200:1
[PE1-vpn-instance-labnario]vpn-target 200:200 both
Configure MP-IBGP between PE routers (PE1 as an example):
[PE1]bgp 200
[PE1-bgp]peer 2.2.2.2 as-number 200
[PE1-bgp] peer 2.2.2.2 connect-interface LoopBack0
[PE1-bgp] peer 3.3.3.3 as-number 200
[PE1-bgp] peer 3.3.3.3 connect-interface LoopBack0
[PE1-bgp]ipv4-family vpnv4
[PE1-bgp-af-vpnv4]policy vpn-target
[PE1-bgp-af-vpnv4]peer 2.2.2.2 enable
[PE1-bgp-af-vpnv4]peer 3.3.3.3 enable
[PE1]dis bgp vpnv4 all peer
BGP local router ID : 10.0.0.2
Local AS number : 200
Total number of peers : 2 Peers in established state : 2
Peer V AS MsgRcvd MsgSent OutQ Up/Down State Pref Rcv
2.2.2.2 4 200 20 19 0 00:15:03 Established 4
3.3.3.3 4 200 20 18 0 00:15:17 Established 4
Configure EBGP between CE and PE2/PE3 routers:
[PE2]bgp 200
[PE2-bgp]ipv4-family vpn-instance labnario
[PE2-bgp-labnario]peer 200.0.0.1 as-number 65001
[PE2-bgp-labnario]import-route direct
[PE3]bgp 200
[PE3-bgp]ipv4-family vpn-instance labnario
[PE3-bgp-labnario]peer 200.0.1.1 as-number 65001
[PE3-bgp-labnario]import-route direct
[CE]bgp 65001
[CE-bgp]peer 200.0.0.2 as-number 200
[CE-bgp] peer 200.0.1.2 as-number 200
[CE-bgp]import-route direct
[CE]dis bgp peer
BGP local router ID : 200.0.0.1
Local AS number : 65001
Total number of peers : 2 Peers in established state : 2
Peer V AS MsgRcvd MsgSent OutQ Up/Down State Pref Rcv
200.0.0.2 4 200 26 31 0 00:22:35 Established 2
200.0.1.2 4 200 26 31 0 00:22:35 Established 2
Let’s check IP routing table on PE1 router:
[PE1]dis ip rout vpn-instance labnario
Route Flags: R - relay, D - download to fib
------------------------------------------------------------------------------
Routing Tables: labnario
Destinations : 6 Routes : 6
Destination/Mask Proto Pre Cost Flags NextHop Interface
4.4.4.4/32 IBGP 255 0 RD 2.2.2.2 GigabitEthernet0/0/1
172.16.10.10/32 IBGP 255 0 RD 2.2.2.2 GigabitEthernet0/0/1
200.0.0.0/24 IBGP 255 0 RD 2.2.2.2 GigabitEthernet0/0/1
200.0.1.0/24 IBGP 255 0 RD 3.3.3.3 GigabitEthernet0/0/2
255.255.255.255/32 Direct 0 0 D 127.0.0.1 InLoopBack0
As we can see, a network 172.16.10.10/32, advertised by CE router, is available on PE1 in VPN instance labnario, with next hop 2.2.2.2 (PE2).
[PE1]dis ip routing-table vpn-instance labnario 172.16.10.10 verbose
Route Flags: R - relay, D - download to fib
------------------------------------------------------------------------------
Routing Table : labnario
Summary Count : 1
Destination: 172.16.10.10/32
Protocol: IBGP Process ID: 0
Preference: 255 Cost: 0
NextHop: 2.2.2.2 Neighbour: 2.2.2.2
State: Active Adv Relied Age: 00h00m43s
Tag: 0 Priority: low
Label: 1026 QoSInfo: 0x0
IndirectID: 0x6
RelayNextHop: 10.0.0.1 Interface: GigabitEthernet0/0/1
TunnelID: 0x1 Flags: RD
Based on the traditional BGP/MPLS VPN technology, both PE2 and PE3 advertise the routes destined for CE to PE1, and allocate private network labels. PE1 then selects a VPNv4 route from MP-BGP neighbors according to the policy. The preferred route, in this example, is the one advertised by PE2.
In case of a fault occurs on PE2, PE1 detects the fault of PE2, re-selects the route advertised by PE3, and updates the forwarding entry. This results in the interruption of end-to-end services due to long convergence time.
Configure VPN FRR policy:
[PE1]ip ip-prefix vpn_frr index 10 permit 2.2.2.2 32
[PE1]route-policy vpn_frr permit node 10
Info: New Sequence of this List.
[PE1-route-policy] if-match ip next-hop ip-prefix vpn_frr
[PE1-route-policy] apply backup-nexthop 3.3.3.3
Enable VPN FRR:
[PE1]ip vpn-instance labnario
[PE1-vpn-instance-labnario]vpn frr route-policy vpn_frr
Configure BFD multi-hop detection between PE1 and PE2 (PE1 as an example):
[PE1]bfd to_pe2 bind peer-ip 2.2.2.2
[PE1-bfd-session-to_pe2] discriminator local 100
[PE1-bfd-session-to_pe2] discriminator remote 200
[PE1-bfd-session-to_pe2] commit
[PE1]dis bfd session all
--------------------------------------------------------------------------------
Local Remote PeerIpAddr State Type InterfaceName
--------------------------------------------------------------------------------
100 200 2.2.2.2 Up S_IP_PEER -
--------------------------------------------------------------------------------
Total UP/DOWN Session Number : 1/0
Let’s check IP routing table in VRF once again:
[PE1]dis ip routing-table vpn-instance labnario 172.16.10.10 verbose
Route Flags: R - relay, D - download to fib
------------------------------------------------------------------------------
Routing Table : labnario
Summary Count : 1
Destination: 172.16.10.10/32
Protocol: IBGP Process ID: 0
Preference: 255 Cost: 0
NextHop: 2.2.2.2 Neighbour: 2.2.2.2
State: Active Adv Relied Age: 00h05m54s
Tag: 0 Priority: low
Label: 1026 QoSInfo: 0x0
IndirectID: 0x6
RelayNextHop: 10.0.0.1 Interface: GigabitEthernet0/0/1
TunnelID: 0x1 Flags: RD
BkNextHop: 3.3.3.3 BkInterface: GigabitEthernet0/0/2
BkLabel: 1024 SecTunnelID: 0x0
BkPETunnelID: 0x3 BkPESecTunnelID: 0x0
BkIndirectID: 0x3
Check a backup next hop address. As you can see, loopback IP address of PE3 has been set as the backup next hop. Additionally a backup label has been specified.
VPN FRR ensures fast end-to-end convergence of services, in a VPN where CEs are dual-homed to a PE, in the case of a PE fault. VPN FRR technology is an improvement of the traditional technology. With VPN FRR, PE1 can select the appropriate VPNv4 routes according to the matching rules. For these routes, in addition to information about the preferred routes advertised by PE2, information about the second-best route advertised by PE3 is filled in the forwarding entry. When a fault occures on PE2, BFD session between PE1 and PE2 is going down. Next PE1 router detects that the outer tunnel between PE1 and PE2 is unavailable. If the LSP is unavailable, the forwarding engine uses the forwarding information of the second best route carried in the local forwarding entry to forward packets. This is how VPN FRR works.
Read More »
 Labnario Huawei From Scratch
Labnario Huawei From Scratch