Access Control List ACL
There are five types of ACLs on Huawei devices. Taking CX600 into consideration there are:
- Basic ACL (number ranges from 2000 to 2999) classifies packets based on a source address
- Advanced ACL (number ranges from 3000 to 3999) source address, destination address, source port number, destination port number, and protocol type
- Interface-based ACL (number ranges from 1000 to 1999) classifies packets based on the interface from which the packets are received
- Ethernet Frame Header ACL (number ranges from 4000 to 4099) classifies packets based on source and destination MAC addresses
- User ACL (number ranges from 6000 to 9999) classifies packets based on user groups.
The rules order depends on rule ID and rule matching order. There are two matching orders:
- Configuration order – ACL rules are matched based on their configuration order. Rules IDs can be configured by user or generated by system automatically according to ACL step. By default the system generates 5 as the first rule ID. So the next rule ID will be 10, 15 and so on. Anytime you can configure rule ID manually, for example rule 1 and this rule will be placed before 5. You do not have to delete the whole ACL. Each time you can delete a specific rule without deleting the whole ACL.
- Automatic order – the most precise rule is taking as the first. This is implemented through the comparison of wildcard masks. The system assigns rule IDs automatically.
The default action defined in the ACL rule is deny.
Actually an ACL is used to classify packets. It is not used itself for packets filtering, but we can use it with conjunction with some other functions, such as policy-based routing, firewall and in traffic classification to filter packets.
A simple example of using ACL is to limit incoming calls for VTY user interfaces:
#
acl number 2500
rule 5 permit source 172.16.10.0 0.0.0.255
#
user-interface vty 0 4
acl 2500 inbound
#
<labnario>dis acl 2500
Basic ACL 2500, 1 rule
Acl's step is 5
rule 5 permit source 172.16.3.0 0.0.0.255
Policy-based routing PBR
Let’s assume that we have topology like this:
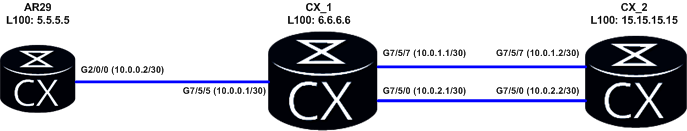
What we have to do is to force router CX_1 to choose interface G7/5/0 and next hop 10.0.2.2 to forward traffic from source IP 5.5.5.5 to destination IP 15.15.15.15. Rest of traffic should go through interface G7/5/7.
Configure IP addresses based on this topology.
Use OSPF protocol to ensure communication in tested network. Let’s take CX_1 as an example:
#
ospf 1 router-id 6.6.6.6
area 0.0.0.0
network 10.0.1.0 0.0.0.3
network 10.0.2.0 0.0.0.3
network 10.0.0.0 0.0.0.3
network 6.6.6.6 0.0.0.0
#
Configure OSPF for the remaining routers.
Increase OSPF cost of one of the links between CX_1 and CX_2 to exclude load-balancing:
#
interface GigabitEthernet7/5/0
ospf cost 100
#
Display routing-table of AR29 to check if all necessary subnets are available through OSPF (display ip routing-table).
Configure ACL on CX_1 which permits IP source 5.5.5.5 to send packets to destination IP 15.15.15.15:
[CX_1]acl number 3000
[CX_1-acl-3000}rule 5 permit ip source 5.5.5.5 0 destination 15.15.15.15 0
Configure traffic classifier and traffic behavior for classified packets:
#
traffic classifier labnario
if-match acl 3000
#
traffic behavior labnario
redirect ip-nexthop 10.0.2.2 interface GigabitEthernet7/5/0
#
Configure traffic policy and assign it to interface G7/5/5 as inbound:
#
traffic policy labnario
statistics enable
classifier labnario behavior labnario
#
interface GigabitEthernet7/5/5
traffic-policy labnario inbound
#
Let’s check now what the result of such traffic policy is. On AR29 router we can use tracert command to check how traffic is going to 15.15.15.15.
<AR29>tracert -a 5.5.5.5 15.15.15.15
traceroute to 15.15.15.15(15.15.15.15), max hops: 30, packet length: 40, press CTRL_C to break
1 10.0.0.1 4 ms 2 ms 7 ms
2 10.0.2.2 3 ms 4 ms 5 ms
As we can see traffic policy is working correctly choosing 10.0.2.2 as the IP next hop.
Now we can try the same but without source IP 5.5.5.5:
<AR29>tracert 15.15.15.15
traceroute to 15.15.15.15(15.15.15.15), max hops: 30, packet length: 40, press CTRL_C to break
1 10.0.0.1 3 ms 1 ms 1 ms
2 10.0.1.2 3 ms 2 ms 2 ms
We can see that policy-based routing is working properly for traffic classified in ACL 3000. Rest of traffic is choosing a route based on IP routing table.
We can also check statistics for this traffic policy. We can use ping for such purposes. Use ping from AR29 and check statistics on CX_1:
<AR29>ping -a 5.5.5.5 -c 100 -m 100 15.15.15.15
<CX_1>display traffic policy statistics interface g 7/5/5 inbound
Info: The statistics is shared because the policy is shared.
Interface: GigabitEthernet7/5/5
Traffic policy inbound: labnario
Traffic policy applied at 2012-02-06 16:15:04
Statistics enabled at 2012-02-06 16:15:16
Statistics last cleared: 2012-02-06 20:14:59
Rule number: 4 IPv4, 0 IPv6
Current status: OK!
Item Packets Bytes
-------------------------------------------------------------------
Matched 100 10,200
+--Passed 100 10,200
+--Dropped 0 0
+--Filter 0 0
+--URPF 0 0
+--CAR 0 0
Missed 19 2,640
Last 30 seconds rate
Item pps bps
-------------------------------------------------------------------
Matched 0 0
+--Passed 0 0
+--Dropped 0 0
+--Filter 0 0
+--URPF 0 0
+--CAR 0 0
Missed 0 288
<AR29>ping -c 100 -m 100 15.15.15.15
<CX_1>dis traffic policy statistics interface g 7/5/5 inbound
Info: The statistics is shared because the policy is shared.
Interface: GigabitEthernet7/5/5
Traffic policy inbound: labnario
Traffic policy applied at 2012-02-06 16:15:04
Statistics enabled at 2012-02-06 16:15:16
Statistics last cleared: 2012-02-06 20:14:59
Rule number: 4 IPv4, 0 IPv6
Current status: OK!
Item Packets Bytes
-------------------------------------------------------------------
Matched 100 10,200
+--Passed 100 10,200
+--Dropped 0 0
+--Filter 0 0
+--URPF 0 0
+--CAR 0 0
Missed 126 13,956
Last 30 seconds rate
Item pps bps
-------------------------------------------------------------------
Matched 0 0
+--Passed 0 0
+--Dropped 0 0
+--Filter 0 0
+--URPF 0 0
+--CAR 0 0
Missed 3 2,648
You can also configure policy-based routing in MPLS L3VPN to allow some IP traffic (based on ACL) from one VPN to be redirected to another VPN. Maybe I will show you such configuration in the future.
Any questions or comments are welcome.
Read More »
 Labnario Huawei From Scratch
Labnario Huawei From Scratch