How to secure communication between two sites connected to the Internet?
Use Site-to-Site IPsec VPN tunnel between two Huawei routers. IPsec VPN is an open standard protocol suite, defined by the IETF in the following RFCs: 2401, 2402-2412, 2451. IPSec is a widely used protocol for securing traffic on IP networks, including the Internet. IPSec can encrypt data between various devices, including router to router, firewall to router, desktop to router, and desktop to server.
How to configure IPsec VPN using Huawei CLI?
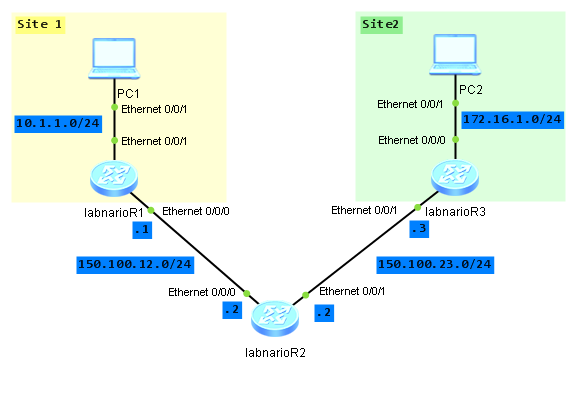
Let’s assume that we have two sites, Site1 and Site2. Both sites have PCs connected to the LAN network, PC1 and PC2 respectively. The sites are connected through WAN network (in our case labnarioR2 router simulates WAN). We want to secure communication between PC1 and PC2. To do so, we have to configure IPSec VPN tunnel between both sites. In our case tunnel will be established between labnarioR1 and labnarioR3 routers. Both routers will be responsible for data encryption and decryption using specified algorithms.
To secure IPSec tunnel, I will use:
- shared key between labnarioR1 and labnarioR3 routers
- ESP protocol for security algorithms negotiation
- SHA1 for authentication and 3DES for encryption
- IKE for key exchange and SA establishment.
Traffic encryption/decryption will be done on both, labnarioR1 and labnarioR3 routers. So I have to configure those two routers, to be able to establish IPsec VPN tunnel. LabnarioR2 router simulates WAN cloud. It has nothing to do with IPSec.
Do not forget to provide IP connectivity between routers and PCs. This is omitted here.
I want to encrypt IP traffic travelling between LAN networks 10.1.1.0/24 and 172.16.1.0/24. To do so, I need to match this traffic using ACL on labnarioR1 and labnarioR3:
[labnarioR1]acl 3000 [labnarioR1-acl-adv-3000]rule 10 permit ip source 10.1.1.0 0.0.0.255 destination 172.16.1.0 0.0.0.255 [labnarioR3]acl 3000 [labnarioR3-acl-adv-3000]rule 10 permit ip source 172.16.1.0 0.0.0.255 destination 10.1.1.0 0.0.0.255
Now I can configure IPSec proposal and define the following parameters:
- Packet encapsulation format (tunnel or transport, I will use tunnel as this is site-to-site model)
- Security protocol (I will use ESP)
- Encryption and authentication algorithms (as mentioned above, SHA1 and 3DES respectively).
[labnarioR1]ipsec proposal PROPOSAL1 [labnarioR1-ipsec-proposal-PROPOSAL1]encapsulation-mode tunnel [labnarioR1-ipsec-proposal-PROPOSAL1]transform esp [labnarioR1-ipsec-proposal-PROPOSAL1]esp authentication-algorithm sha1 [labnarioR1-ipsec-proposal-PROPOSAL1]esp encryption-algorithm 3des
To define IKE peer:
[labnarioR1]ike peer PEER-LABNARIOR3 V1 [labnarioR1-ike-peer-PEER-LABNARIOR3]pre-shared-key simple LaBnArIoKeY [labnarioR1-ike-peer-PEER-LABNARIOR3]remote-address 150.100.23.3
Now I can define IPSec policy:
[labnarioR1]ipsec policy POLICY1 10 isakmp [labnarioR1-ipsec-policy-isakmp-POLICY1-10]proposal PROPOSAL1 [labnarioR1-ipsec-policy-isakmp-POLICY1-10]security acl 3000 [labnarioR1-ipsec-policy-isakmp-POLICY1-10]ike-peer PEER-LABNARIOR3
To attach IPSec policy to my WAN interface:
[labnarioR1]int Ethernet0/0/0 [labnarioR1-Ethernet0/0/0]ipsec policy POLICY1
The same configuration should be done on labnarioR3 router:
# ipsec proposal PROPOSAL1 esp authentication-algorithm sha1 esp encryption-algorithm 3des # ike peer PEER-LABNARIOR1 v1 pre-shared-key simple LaBnArIoKeY remote-address 150.100.12.1 # ipsec policy POLICY1 10 isakmp security acl 3000 ike-peer PEER-LABNARIOR1 proposal PROPOSAL1 # interface Ethernet0/0/1 ip address 150.100.23.3 255.255.255.0 ipsec policy POLICY1
To bring IPsec VPN tunnel up, IP traffic should be generated between PC1 and PC2. To do so, just ping PC2 from PC1 or vice versa. Let’s verify if our tunnel is up.
To display IKE security associations:
[labnarioR1]display ike sa
Conn-ID Peer VPN Flag(s) Phase
---------------------------------------------------------------
52 150.100.23.3 0 RD|ST 2
28 150.100.23.3 0 RD|ST 1
Flag Description:
RD--READY ST--STAYALIVE RL--REPLACED FD--FADING TO--TIMEOUT
HRT--HEARTBEAT LKG--LAST KNOWN GOOD SEQ NO. BCK--BACKED UP
To display IPsec security associations:
[labnarioR1]display ipsec sa brief
Number of SAs:0
Src address Dst address SPI VPN Protocol Algorithm
-------------------------------------------------------------------------------
150.100.23.3 150.100.12.1 641342674 0 ESP E:3DES A:SHA1-96
150.100.12.1 150.100.23.3 228173657 0 ESP E:3DES A:SHA1-96
To check if traffic between PC1 and PC2 is travelling through VPN tunnel, check ACL matchings and IKE/IPsec packets statistics:
[labnarioR1]dis acl 3000 Advanced ACL 3000, 1 rule ACL's step is 5 rule 10 permit ip source 10.1.1.0 0.0.0.255 destination 172.16.1.0 0.0.0.255 (10 times matched) [labnarioR1]dis ike statistics v1 ---------------------------------------------------------- IKE V1 statistics information Number of total peers : 18 Number of policy peers : 1 Number of profile peers : 17 Number of proposals : 1 Number of established V1 phase 1 SAs : 1 Number of established V1 phase 2 SAs : 1 Number of total V1 phase 1 SAs : 1 Number of total V1 phase 2 SAs : 1 Number of total SAs : 2 Keep alive time : 0 Keep alive interval : 0 keepalive spi list : Disable ---------------------------------------------------------- [labnarioR1]dis ipsec statistics esp Inpacket count : 3435973836 Inpacket auth count : 3435973836 Inpacket decap count : 3435973836 Outpacket count : 3435973836 Outpacket auth count : 3435973836 Outpacket encap count : 3435973836 Inpacket drop count : 3435973836 Outpacket drop count : 3435973836 BadAuthLen count : 3435973836 AuthFail count : 3435973836 PktDuplicateDrop count : 3435973836 PktSeqNoTooSmallDrop count: 3435973836 PktInSAMissDrop count : 3435973836
As you see, IPsec statistics look a little bit strange. This is because these commands were done on eNSP. It looks like IPsec is not working on eNSP even though there are all configuration and display commands. When tested on AR19 routers, everything was fine.
Debugging commands:
<labnarioR1>debugging ike ? all All IKE debugging functions dpd IKE debug for dpd error Error debugging functions exchange IKE exchange debugging functions message IKE message debugging functions misc All other debugging functions packet IKE packet content debugging function sa Security Association sysdep Information with IPSec debugging functions task IKE debug for main task entry transport Transport debugging functions xauth Information with IPSec debugging functions <labnarioR1>debugging ipsec ? all All switches hw Hardware infomation misc All other debugging function packet Packet debugging function sa SA debugging function
Final configs:
sysname labnarioR1 # acl number 3000 rule 10 permit ip source 10.1.1.0 0.0.0.255 destination 172.16.1.0 0.0.0.255 # ipsec proposal PROPOSAL1 esp authentication-algorithm sha1 esp encryption-algorithm 3des # ike peer PEER-LABNARIOR3 v1 pre-shared-key simple LaBnArIoKeY remote-address 150.100.23.3 # ipsec policy POLICY1 10 isakmp security acl 3000 ike-peer PEER-LABNARIOR3 proposal PROPOSAL1 # interface Ethernet0/0/0 ip address 150.100.12.1 255.255.255.0 ipsec policy POLICY1 sysname labnarioR3 # acl number 3000 rule 10 permit ip source 172.16.1.0 0.0.0.255 destination 10.1.1.0 0.0.0.255 # ipsec proposal PROPOSAL1 esp authentication-algorithm sha1 esp encryption-algorithm 3des # ike peer PEER-LABNARIOR1 v1 pre-shared-key simple LaBnArIoKeY remote-address 150.100.12.1 # ipsec policy POLICY1 10 isakmp security acl 3000 ike-peer PEER-LABNARIOR1 proposal PROPOSAL1 interface Ethernet0/0/1 ip address 150.100.23.3 255.255.255.0 ipsec policy POLICY1
 Labnario Huawei From Scratch
Labnario Huawei From Scratch
i am not getting ping from PC1 to PC2. display ipsec sa brief, display ike sa are showing same but still PC1 to PC2 request timeout. PC is getting ping to correaponding gateway.
Hi,
create static routes via these tunnel interfaces to PC-networks.