Some time ago I wrote about local PBR and interface PBR.
It’s time to talk about routing policy, that is a different mechanism. Routing policy is applied to routing information and it is combined with routing protocols to form policies. PBR mechanism is applied to data flows and and packets are forwarded according to the configured policy.
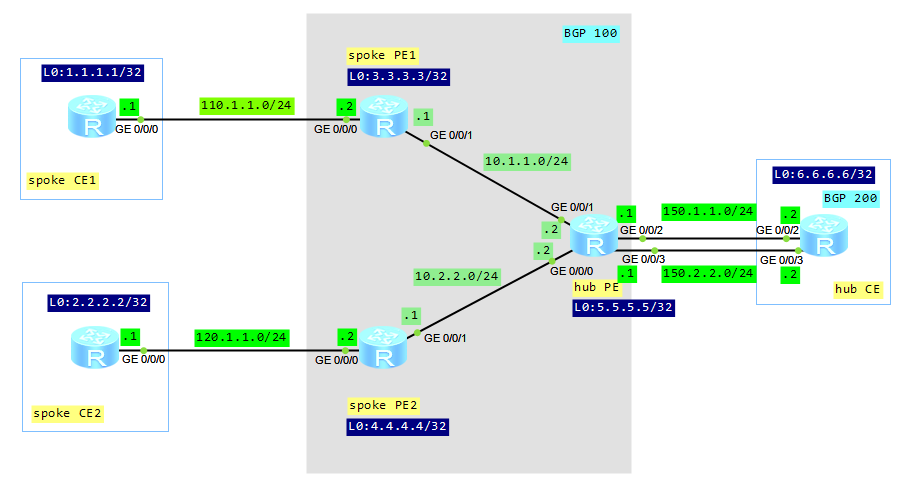
Routing policy is a tool which can be used to filter routes and set route attributes, when importing routing information into OSPF, RIP, ISIS or BGP protocols. BGP can use routing policy to filter advertising routes as well. Routing policy defines which of the routes from the specific routing protocol are allowed to be imported into the target routing protocol. It can be also used to match routes or certain route attributes and to change these attributes when the matching rules are met.
Routing policy command syntax:
route-policy route-policy-name { permit | deny } node node
A route-policy may consists of multiple nodes, for example:
route-policy LABNARIO-POLICY permit node 10 route-policy LABNARIO-POLICY deny node 20
 Labnario Huawei From Scratch
Labnario Huawei From Scratch