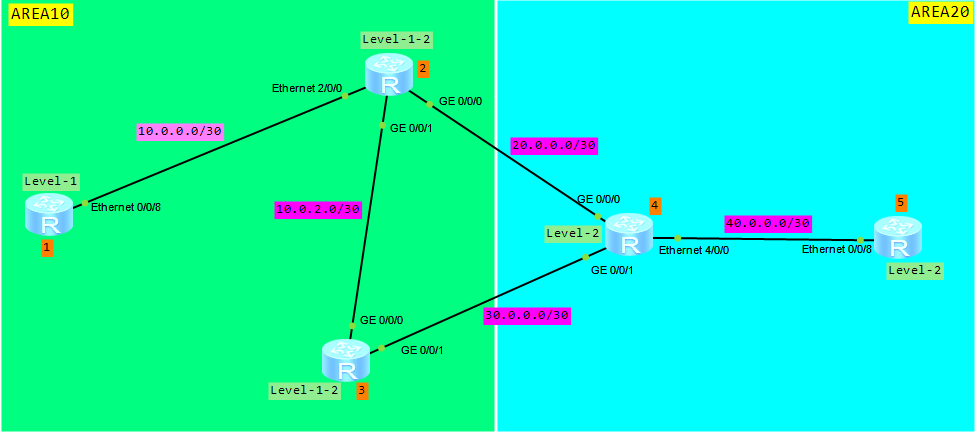
Let’s keep going and try to configure ISIS route aggregation based on the following topology:
If you want to recall how to configure ISIS adjacency on Huawei routers, just go to ‘ISIS on Huawei routers‘.
To avoid DIS election, configure all physical interfaces as ISIS point-to-point (p2p) links (Router 1 as an example):
[1-Ethernet0/0/8]isis circuit-type p2p
[1]dis isis interface
Interface information for ISIS(1)
---------------------------------
Interface Id IPV4.State IPV6.State MTU Type DIS
Eth0/0/8 003 Up Down 1497 L1/L2 --
Loop0 001 Up Down 1500 L1/L2 --
Loop100 002 Up Down 1500 L1/L2 --
 Labnario Huawei From Scratch
Labnario Huawei From Scratch