The last article dealt with outbound NAT. Let’s focus today on NAT server. NAT server enables private network servers to provide services for external networks with public IP addresses. In this lab, our enterprise provides FTP services for external users.
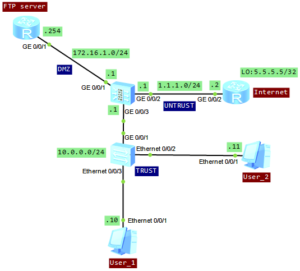
We can use the topology from the last post:
In our case AR router works as FTP server:
# FTP server enable aaa local-user labnario password cipher qGj8!H#yx.ajUn1vMEIB1lG# local-user labnario privilege level 3 local-user labnario ftp-directory flash: local-user labnario service-type ftp # interface GigabitEthernet0/0/1 ip address 172.16.1.254 255.255.255.0 # ip route-static 0.0.0.0 0.0.0.0 172.16.1.1
Configuration of Internet router:
# interface GigabitEthernet0/0/2 ip address 1.1.1.2 255.255.255.0 # ip route-static 1.1.1.100 255.255.255.255 1.1.1.1
Firewall USG5500 configuration
Set IP addresses of interfaces and add them to proper security zones:
[SRG]dis current-configuration interface GigabitEthernet # interface GigabitEthernet0/0/1 ip address 172.16.1.1 255.255.255.0 # interface GigabitEthernet0/0/2 ip address 1.1.1.1 255.255.255.0 [SRG]display current-configuration configuration zone # firewall zone untrust set priority 5 add interface GigabitEthernet0/0/2 # firewall zone dmz set priority 50 add interface GigabitEthernet0/0/1
Configure interzone packet filtering to ensure that users in Untrust zone can access the FTP server in DMZ zone:
[SRG]display current-configuration configuration policy-interzone # policy interzone dmz untrust inbound policy 1 action permit policy service service-set ftp policy destination 172.16.1.254 0
Configure internal server. Create a mapping relation between public and private IP addresses of FTP server:
[SRG]nat server 0 protocol tcp global 1.1.1.100 ftp inside 172.16.1.254 ftp
Configure the NAT ALG function for the DMZ-Untrust interzone to ensure that the server provides FTP services for extranet users normally:
[SRG]display current-configuration configuration interzone # firewall interzone dmz untrust detect ftp
What is NAT ALG for? NAT translates only IP addresses in IP packet headers and port information in TCP/UDP packet headers. In our case, the firewall must identify the IP address and port number in the payload field of the FTP application, to continue NAT processing. Without NAT ALG, the NAT process fails.
Verification of NAT server
[SRG]display firewall session table verbose Current Total Sessions : 1 ftp VPN:public --> public Zone: untrust--> dmz TTL: 00:10:00 Left: 00:09:52 Interface: GigabitEthernet0/0/1 NextHop: 172.16.1.254 MAC: 54-89-98-91-56-e2 <--packets:6 bytes:363 -->packets:8 bytes:364 1.1.1.2:61428+->1.1.1.100:21[172.16.1.254:21] [SRG]display nat server Server in private network information: id : 0 zone : --- interface : --- global-start-addr : 1.1.1.100 global-end-addr : --- inside-start-addr : 172.16.1.254 inside-end-addr : --- global-start-port : 21(ftp) global-end-port : --- insideport : 21(ftp) globalvpn : public insidevpn : public protocol : tcp vrrp : --- no-reverse : no Total 1 NAT servers [SRG]display firewall server-map 11:30:50 2015/04/22 server-map item(s) ------------------------------------------------------------------------------ Nat Server, any -> 1.1.1.100:21[172.16.1.254:21], Zone: --- Protocol: tcp(Appro: ftp), Left-Time: --:--:--, Addr-Pool: --- VPN: public -> public Nat Server Reverse, 172.16.1.254[1.1.1.100] -> any, Zone: --- Protocol: any(Appro: ---), Left-Time: --:--:--, Addr-Pool: --- VPN: public -> public <Internet>ftp 1.1.1.100 Trying 1.1.1.100 ... Press CTRL+K to abort Connected to 1.1.1.100. 220 FTP service ready. User(1.1.1.100:(none)):labnario 331 Password required for labnario. Enter password: 230 User logged in. [ftp]
 Labnario Huawei From Scratch
Labnario Huawei From Scratch
Thank you. I benefited from your post