It’s time to check a firewall available in eNSP simulator. Today a simple task, just configuring inter-VLAN communication on Huawei USG5500.
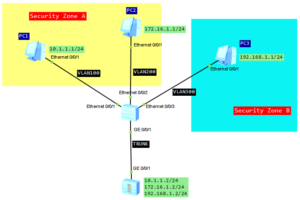
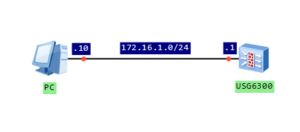
Let’s look at the following topology:
Configuration roadmap:
- Configure L2 communication on the switch.
- As the switch is L2, configure subinterfaces on the firewall and enable L3 communication between different VLANs.
- Set IP addresses and gateways for all PCs.
- Create 2 security zones and configure interzone packet-filterfing to control traffic between VLANs.
- Security requirements for the network:
- PC1 in VLAN100 and PC2 in VLAN200 can communicate each other.
- PC3 in VLAN300 can access PC1 and PC2. PC1 and PC2 cannot access PC3.
 Labnario Huawei From Scratch
Labnario Huawei From Scratch