Let’s assume that a large number of packets are sent to CPU of a device. What will happen if most of these packets are malicious attack packets? CPU usage will become high, what can bring to services’ deterioration. In extreme cases it can lead the device to reboot. We can minimize an impact of the attack on network services, providing the local attack defense function. When such attack occurs, this function ensures non-stop service transmission.
Attack Defense Policy Supported by AR routers:
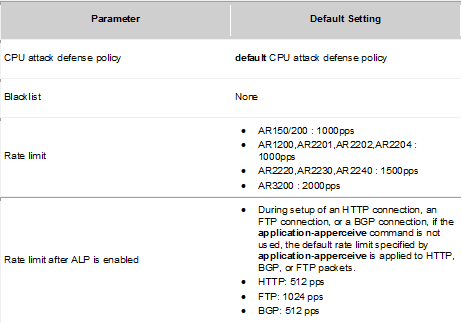
CPU attack defense:
- The device uses blacklists to filters invalid packets sent to the CPU
- The device limits the rate of packets sent to the CPU based on the protocol type
- The device schedules packets sent to the CPU based on priorities of protocol packets
- The device uniformly limits the rate of packets with the same priority sent to the CPU and randomly discards the excess packets to protect the CPU
- ALP is enabled to protect HTTP, FTP and BGP sessions. Packets matching characteristics of the sessions are sent at a high rate, that’s why session-related services are ensured.
Attack source tracing:
- Attack source tracing checks attack packets sent to the CPU and notifies the administrator by sending logs or alarms so that the administrator can take measures to defend against attacks.
Although each device has the defult configuration of local attack defense policy, you can change it every time you need.
Based on AR documentation:
Default configuration of attack source tracing:
Default configuration of CPU attack defense:
Configuring attack source tracing:
Creating an attack defense policy:
cpu-defend policy policy-name (max 19 attack defense policies including the defualt)
Configuring the threshold for attack source tracing:
auto-defend enable auto-defend threshold threshold-value
Configuring the alarm function for attack source tracing:
auto-defend alarm enable auto-defend alarm threshold threshold-value
Configuring CPU Attack Defense:
Configuring a blacklist:
blacklist blacklist-id acl acl-number (how to configure ACL)
Configuring the rate limit for packets sent to the CPU:
packet-type packet-type rate-limit rate-value (excess packets are discarded) deny packet-type packet-type (discards all packets)
Setting the priority for packets of a specified protocol:
packet-type packet-type priority priority-level
Configuring ALP:
application-apperceive packet-type { bgp | ftp | http } rate-limit rate-value
Configuring the rate limit for all packets sent to the CPU:
rate-limit all-packets pps pps-value
Applying the attack defense policy:
cpu-defend-policy policy-name [ global | slot slot-id ] [AR3200]cpu-defend-policy labnario (apply the CPU attack defense policy to the SRU) [AR3200]cpu-defend-policy labnario global (apply the CPU attack defense policy to the LPU) [AR3200]cpu-defend-policy labnario slot 2 (apply the CPU attack defense policy to slot 2)
Useful maintenace commands:
- display auto-defend attack-source
- display auto-defend configuration
- display cpu-defend policy
- display cpu-defend policy
- display cpu-defend statistics
- display cpu-defend configuration.
 Labnario Huawei From Scratch
Labnario Huawei From Scratch