Some time ago I wrote about local PBR and interface PBR.
It’s time to talk about routing policy, that is a different mechanism. Routing policy is applied to routing information and it is combined with routing protocols to form policies. PBR mechanism is applied to data flows and and packets are forwarded according to the configured policy.
Routing policy is a tool which can be used to filter routes and set route attributes, when importing routing information into OSPF, RIP, ISIS or BGP protocols. BGP can use routing policy to filter advertising routes as well. Routing policy defines which of the routes from the specific routing protocol are allowed to be imported into the target routing protocol. It can be also used to match routes or certain route attributes and to change these attributes when the matching rules are met.
Routing policy command syntax:
route-policy route-policy-name { permit | deny } node node
A route-policy may consists of multiple nodes, for example:
route-policy LABNARIO-POLICY permit node 10 route-policy LABNARIO-POLICY deny node 20
The relationship between the nodes of a route-policy is „OR”. This means that if a route matches the node 10 command, the route will not be matched against the node 20. If a route does not match any node, the route fails to match the route-policy. If two nodes are configured, a route is first matched with the node 10 command.
A node in a route-policy can use:
- permit parameter – If a route matches the node, the router performs actions defined by the apply clauses and the matching is complete. Otherwise, the route continues to match the next node.
- deny parameter – in this mode the apply clauses are not used. If a route entry matches all the if-match clauses of the node, the route is denied by the node and the next node is not matched. If the entry does not match all the clauses, the next node is matched.
It is important to note that:
- by default, routes that are unmatched by the nodes, will be denied
- if multiple nodes are defined, at least one of them should use permit parameter
- if all the nodes are in deny mode, all the routes will be denied by the route-policy
- if no if-match clause is defined, all the routes meet the matching rules
Each node can be classified into the following clauses:
- if-match – match certain route attributes
- apply – set certain route attributes
The relationship between the if-match clauses is “AND”. This means that a route must match all the if-match clauses.
If-match clauses can match the following:
acl Specify an ACL as-path-filter BGP AS path list community-filter Match BGP community filter cost Match metric of route extcommunity-filter Match BGP/VPN extended community filter interface Specify the interface matching the first hop of routes ip IP information group-address Match group address of route next-hop Match next-hop address of route route-source Match advertising source address of route ip-prefix Specify an address prefix-list ipv6 IPv6 Information group-address Match group address of route next-hop Match next-hop address of route route-source Match advertising source address of route mpls-label Give the Label rd-filter Route-distinguisher filter route-type Match route-type of route external-type1 OSPF External Type 1 routes external-type1or2 OSPF External routes (OSPF type 1/2) external-type2 OSPF External Type 2 routes internal Internal route (including OSPF intra/inter area) is-is-level-1 IS-IS Level-1 routes is-is-level-2 IS-IS Level-2 routes nssa-external-type1 OSPF NSSA External Type1 routes nssa-external-type1or2 OSPF NSSA External Type1 and Type2 routes nssa-external-type2 OSPF NSSA External Type2 routes tag Match tag of route
Apply clauses can set the following:
[Labnario-route-policy]apply ?
as-path BGP AS path list
backup-interface Backup outgoing interface
backup-nexthop Backup nexthop address
behavior Specify QoS policy as behavior
comm-filter Set BGP community filter (for deletion)
community BGP community attribute
cost Set metric of route
cost-type Type of metric for destination routing protocol
external IS-IS external metric
internal IS-IS internal metric/Set BGP MED to IGP metric of nexthop
type-1 OSPF External Type 1 routes
type-2 OSPF External Type 2 routes
dampening Set BGP route flap dampening parameters
extcommunity Set BGP/VPN extended community filter
ip-address IP information
next-hop Next hop address
ip-precedence Specify QoS policy as IP precedence
ipv6 IPv6 Information
next-hop Next hop address
isis Where to import route
level-1 Import into a level-1 area
level-1-2 Import into level-1 and level-2
level-2 Import into level-2 sub-domain
local-preference BGP local preference path attribute
mpls-label Give the Label
origin BGP origin code
egp Remote EGP
igp Local IGP
incomplete Unknown heritage
ospf Where to import route
backbone Import into OSPF backbone area
stub-area Import into OSPF NSSA area
preference Give the Preference (Route Preference)
preferred-value BGP Preferred-value (weight) for routing table
qos-local-id Specify QoS policy as qos local id
tag Set tag of route
traffic-index Specify BGP Traffic Accounting Index
Examples:
Configure a route-policy to import into OSPF:
- routes tagged with a value of 100
- routes tagged with a value of 200
- set them a tag 300
- block any other routes
Configure a route-policy to import into RIP:
- All the OSPF routes except the prefix 120.10.1.0/24, if it comes from the source of 150.100.1.5
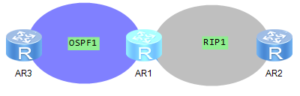
Config should be done on AR1 router, as this is a boundary router between OSPF and RIP domains:
# route-policy RIP-2-OSPF permit node 10 if-match tag 100 apply tag 300 # route-policy RIP-2-OSPF permit node 20 if-match tag 200 apply tag 300 # ospf 1 import-route rip 1 route-policy RIP-2-OSPF # route-policy OSPF-2-RIP deny node 10 if-match ip-prefix PREFIX1 if-match ip route-source acl 2001 # route-policy OSPF-2-RIP permit node 20 # ip ip-prefix PREFIX1 index 10 permit 120.10.1.0 24 # acl number 2001 rule 10 permit source 150.100.1.5 0 # rip 1 import-route ospf 1 route-policy OSPF-2-RIP
 Labnario Huawei From Scratch
Labnario Huawei From Scratch