NAP is a Huawei proprietary protocol, which implements remote configuration in Layer 3 networks. It allows to log into an unconfigured device from a directly connected device. It is very simple and can be really helpful, when implementing new devices. NAP establishes a temporary neighbor relationship between configured and unconfigured devices. Both must be directly connected through a physical link. When NAP relationship is established, telnet can be done to the unconfigured device.
NAP relationship can be established in two different ways:
- Automatically – using IP addresses allocated by the system
- Statically – using IP addresses allocated by the administrator.
NAP cannot be used on interfaces, configured with commands affecting the IP address configuration or IP packet forwarding, such as commands related to VPNs or Ethernet trunks.
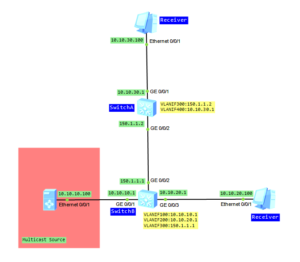
How to use NAP? Let’s assume that we have two switches as in the picture below:
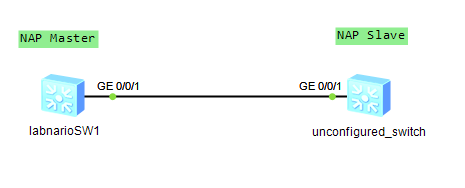
 Labnario Huawei From Scratch
Labnario Huawei From Scratch