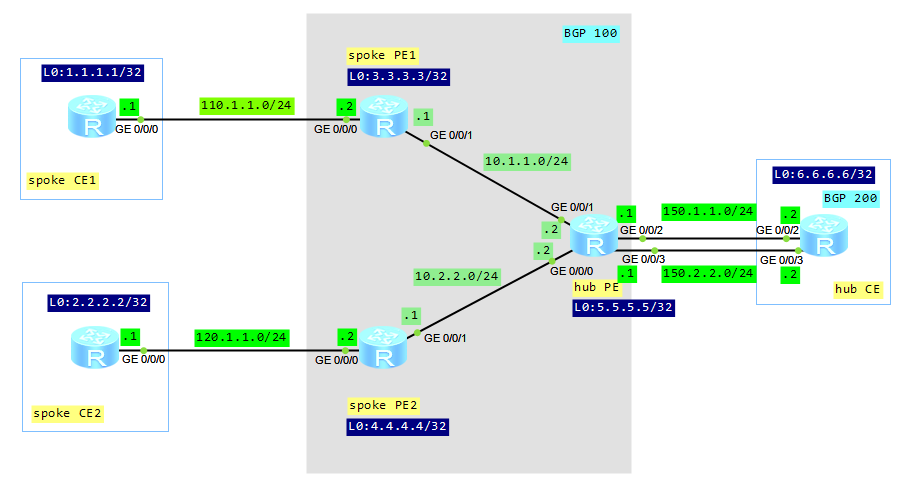
Let’s assume that you have U2000 NMS server to monitor Huawei devices. We can manage these devices in 2 ways: outband or inband management. Outband management means that you have a separate DCN network to manage devices. It is commonly used for critical nodes, for example for backbone routers. Unlike to backbone network, it is difficult to implement DCN for mobile backhaul networks, where the number of devices reaches hundreds or even thousands. In such situation inband management is implemented to reduce cost. Then the decision how to send SNMP packets to the NMS server is based on routing protocols. The packets travel through the monitored network and are susceptible to all turbulences, which can appear in the network. This may lead to the fact that some SNMP packets may be lost by the network.
Let’s imagine such case. A link between a router and NMS is “DOWN”. No redundant link is established. The router sends SNMP trap to the NMS server but the server is not available. The SNMP packet is lost. Then the link is going to “UP” state and the router send SNMP trap to U2000. This trap is then dropped by U2000 because there is not related “DOWN” trap, which was lost before.
And what’s next?
U2000 synchronizes alarms with devices every 30 minutes and NMS server receives “DOWN” trap from the router, which was lost earlier. As the clearing trap was dropped, this “DOWN” alarm will not be cleared anymore. Then we have “DOWN” hanging (not cleared) alarm in U2000.
 Labnario Huawei From Scratch
Labnario Huawei From Scratch